Concept Of TrustZone By ARM

Security is a big challenge for Embedded Hardware, especially for IOT/connected devices. Connection to the internet enables a venue for hacking such as Distributed Denial of Service (DDoS) attacks and unauthorized access to internal networks.
What is TrustZone?
ARM TrustZone is a technology designed to provide hardware-based security features for a wide range of computing devices, with a focus on mobile and embedded systems. It is developed by ARM Holdings, a company known for its semiconductor intellectual property, particularly in the field of microprocessor architecture.
How is it work?
TrustZone creates a secure and non-secure world on a single processor, allowing the isolation of sensitive operations and data from the rest of the system. The concept involves dividing the processor into two virtual processors: the Secure World and the Normal World. The Secure World operates in a trusted execution environment, isolated from the Normal World, where the standard system functions run.
In the normal world, where you would have your typical OS like your android OS or iOS, and you would be running your typical tasks like your WhatsApp or anything else. so, all of them run in this normal world. Now you would have a secure world as well which would run your sensitive task. so, all your sensitive operation such as Storing sensitive data like passwords or key would be handled by the secure world. For example, you would have normal applications and whenever you require to do some sensitive operation, the processor shifts to the secure world. You store your password which gets stored into secure storage areas. Then once it is stored, you switch back to the normal world, and This storage area would never access by normal world. So, ARM provide this environment and manages this switching between normal and secure world.
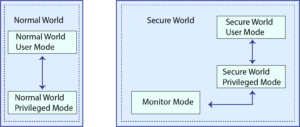
How TrustZone is typically used in firmware?
Secure Boot:
- During the boot process, TrustZone helps establish a secure foundation by supporting secure boot procedures.
- The firmware in the secure world can verify the authenticity and integrity of the bootloader and subsequent firmware components before allowing them to execute.
Secure Storage:
- TrustZone can be employed to create secure storage areas where sensitive data, such as cryptographic keys or other confidential information, can be stored.
- Access to these secure storage areas is restricted to the secure world, providing an additional layer of protection.
Isolated Execution Environments:
- TrustZone enables the creation of a Trusted Execution Environment (TEE), where firmware components and applications can run in an isolated and secure manner.
- Security-critical operations, such as authentication or secure transactions, can be performed within the TEE to protect against attacks from the non-secure world.
Secure Communication:
- TrustZone facilitates secure communication channels between the secure and non-secure worlds.
- This is important for enabling secure interactions between trusted and non-trusted components of the firmware.
Security Services and APIs:
- TrustZone provides security services and APIs (Application Programming Interfaces) that firmware developers can use to implement secure functionalities.
- Developers can leverage these interfaces to access secure resources, perform secure operations, and communicate securely with other components.
Handling Sensitive Operations:
- Firmware running in the secure world, within the TrustZone environment, can handle sensitive operations that require a higher level of security.
- Examples include secure key generation, cryptographic operations, and other secure processing tasks.
Secure Monitor:
- The firmware in the secure world often includes a Secure Monitor, which is responsible for managing the transitions between the secure and non-secure states.
- The Secure Monitor ensures that the system operates securely and that the secure world remains protected from potential threats in the non-secure world.
By incorporating TrustZone into firmware design, developers can enhance the security of embedded systems, protect sensitive information, and mitigate various security threats. This is particularly important in applications where maintaining the integrity and confidentiality of data is critical.
Conclusion:
Incorporating ARM TrustZone into firmware design provides a robust solution for securing embedded systems, crucial in IoT environments. It effectively isolates and manages secure operations, offering a reliable defense against various security threats and ensuring the integrity and confidentiality of critical data.